Digital Age – How to approach Cyber Security
Andreas von Grebmer | CIS Switzerland.
A risk-based approach to information security considering the human factor
In June 2017 a first chapter “Information Security Stumbling Blocks” of the book was released on www.security-finder.ch prior to the finalization of the new release followed by a second extract of the chapter “Traditional Information Security” in December 2017.
In this issue the extract focuses on the confusion between compliance and risk management, bearing the upcoming GDPR in mind which almost shifts all unregulated industries to regulated industries.
2.7 Risk Assessment vs. Compliance
If you work in a highly-regulated environment, such as in the pharmaceutical, financial, or insurance industry, etc., your focus is to comply with the applicable regulations. In discussions with employees from these environments you will notice that they often challenge the effort of performing risk assessments, as they are mainly busy with fulfilling given standards or regulatory (compliance) requirements.
The fact is that compliance activities are not considered as risk management activities. To not be compliant is a risk, and most of the time a big risk. Pharmaceutical companies that do not comply with certain requirements can be banned from delivering certain products to certain countries. Managers not fulfilling the Sarbanes-Oxley (SOX) requirements can be sentenced to jail time. These are risks. If you are compliant with the regulations, you are mitigating these specific risks, but you are not performing risk management. Regulations can require certain measures such as:
- Weight samples every 30 minutes during production.
- Double management signatures on financial reports.
- Audit trail in an IT system.
- Split the knowledge of a password or phase phrase to multiple individuals.
Most of these measures are designed to address responsibility in case of a product failure, misuse, fraud, etc. Only a few regulatory requirements focus on business continuity and the long term sustainable income of your company, and that is what you are looking for when managing risks.
Therefore, compliance supports and amplifies risk reduction in several cases but compliance is not risk management. If it were so, every company which is, for example, ISO certified would no longer have any risks.
Compliance (Management) is not risk management.
You can be up to 100% compliant and still have a high risk exposure and vice versa.
It is important that the residual risk is actively managed.
Ignoring it is not a good strategy.
Diagram 25: Compliance and risk management
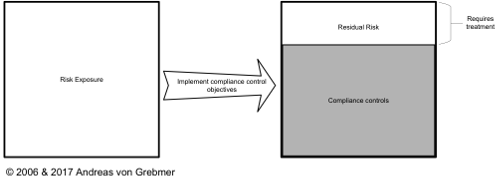
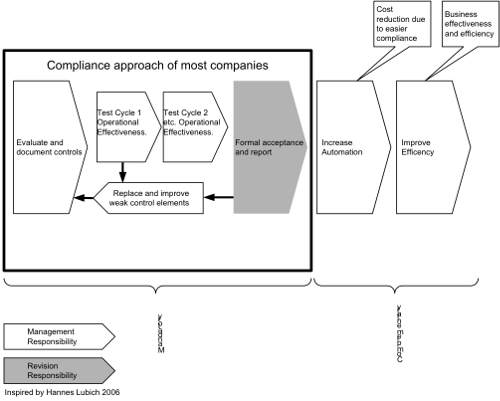
Compliance in itself is not the target!
Diagram 26: Compliance is not the goal
At this stage I would like to emphasize how important it is to know the applicable legislations, law and industry standards that are relevant for your company. The next table gives you an overview of regulations that are relevant for information security and data privacy. Please note you will also need to evaluate if other laws are relevant for your industry and legislation you are doing business in.
It is important that you maintain a radar that allows your organization to forecast what new compliance/regulatory requirements are coming your way.
Diagram 27: Relevant compliance laws and regulations
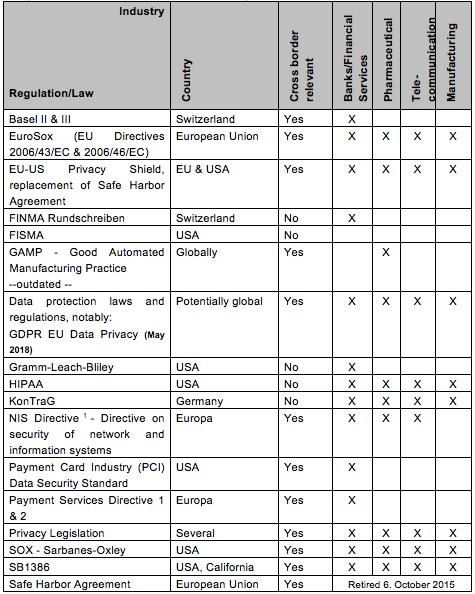
*1 ec.europa.eu: «The NIS Directive was adopted by the European Parliament on 6 July 2016. Member States will have 21 months to transpose the Directive into their national laws and 6 months more to identify operators of essential services. …. a culture of security across sectors which are vital for our economy and society and moreover rely heavily on ICTs, such as energy, transport, water, banking, financial market infrastructures, healthcare and digital infrastructure».
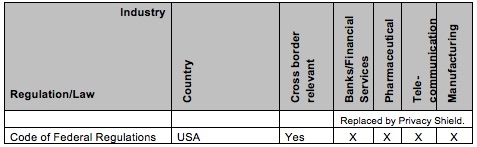
The table above gives you an overview of regulations that are relevant for information security and data privacy. Please note you will also need to evaluate if other laws are relevant for your industry.
One single legislation I would like to outline here is the GDPR, since it has huge impact on the information security activities and focus over the next few years:
Even if you do not understand the hype for data privacy, e.g. because you have a non-EU cultural background, do not underestimate the risks. Especially when the law becomes effective there is a lot of uncertainty since EU member states need to define the details. In some countries, with strong data privacy authorities, you can expect these authorities to make an example of some magnitude to introduce the baseline of what they expect.
Quelle: Text und Grafiken «Digital Age – How to approach Cyber Security»
Erhältlich auf Amazon
Auch als eBook erhältlich.
Verlag: Books on Demand
Autor: Andreas von Grebmer
Erscheinungsjahr: 2017
ISBN: 978-3744871464

































































































